📔 REST API Architecture Principles & Best Practices
Comprehensive guide to REST API architecture principles and best practices — validated from top trusted sources — explained clearly, concisely, and precisely.
🧭 REST API Architecture Principles & Best Practices
I. What is REST? (Overview & Essence)
1. Definition
REST (Representational State Transfer) is an architectural style for building distributed systems, especially web services.
It defines a set of constraints and principles that make systems scalable, stateless, and interoperable over HTTP.
- Coined by: Roy Fielding (in his 2000 PhD dissertation)
- Used in: Web APIs, microservices, IoT, mobile backends, and modern web apps.
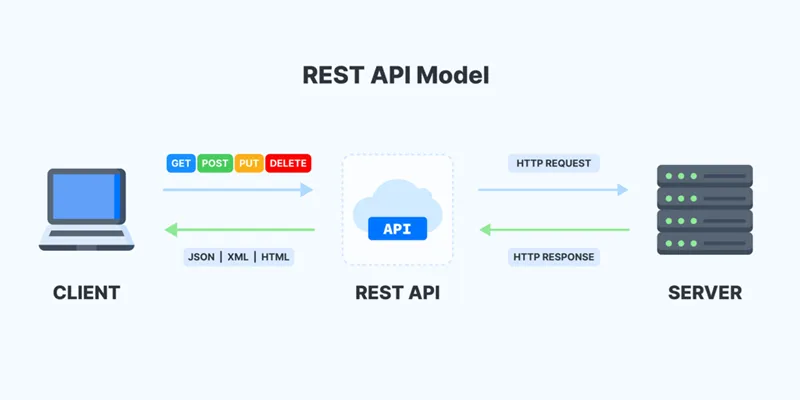
🧱 Core Idea: REST treats everything as a resource (users, orders, files) and uses standard HTTP methods (GET, POST, PUT, DELETE) to operate on them.
2. Key Benefits
| Benefit | Description | Example |
|---|---|---|
| Scalability | Statelessness allows horizontal scaling | Multiple app servers handle requests independently |
| Simplicity | Uses standard HTTP methods | GET /users fetches users |
| Cacheability | Improves performance | Browser caches GET responses |
| Portability | Platform-agnostic communication | Any client (web, mobile) can consume the same API |
II. REST Architectural Constraints (Principles)
REST is defined by six key constraints, validated from Wikipedia and IBM Think.
1. Client-Server Separation
- Principle: Separate frontend (client) from backend (server) logic.
- Rationale: Enables independent evolution — UI can change without changing API logic.
- Example: A React frontend consuming a Flask backend via REST API.
2. Statelessness
- Principle: Each client request must contain all information needed by the server.
- Rationale: No session state stored on the server → easier scalability and reliability.
- Example:
1 2
GET /orders/123 Authorization: Bearer <token>
The server doesn’t rely on prior requests.
3. Cacheability
- Principle: Responses should explicitly indicate if they are cacheable.
- Rationale: Reduces client-server interactions, improving performance.
Implementation:
1
Cache-Control: max-age=3600- Example: Frequently accessed data like
GET /productsis cached.
4. Uniform Interface
- Principle: All interactions follow a standard interface for consistency.
- Rationale: Simplifies client-server interaction and enables generic tools.
| Sub-Constraint | Explanation | Example |
|---|---|---|
| Resource identification | Each resource has a unique URI | /users/123 |
| Resource representation | Data returned as JSON/XML | { "id": 123, "name": "Alice" } |
| Self-descriptive messages | Each message contains enough info to process it | Content-Type: application/json |
| HATEOAS (Hypermedia as the Engine of Application State) | Responses include links to related actions | "links": { "orders": "/users/123/orders" } |
5. Layered System
- Principle: System organized into hierarchical layers (load balancer, cache, app server, DB).
- Rationale: Improves scalability, maintainability, and security.
- Example: Client → API Gateway → Microservice → Database
6. Code on Demand (Optional)
- Principle: Server can send executable code (e.g., JavaScript) to client.
- Rationale: Extends client functionality temporarily.
- Example: Web browser executing server-provided JS snippet.
III. REST vs. RPC vs. SOAP
| Feature | REST | SOAP | RPC |
|---|---|---|---|
| Protocol | HTTP (mostly) | XML-based | HTTP, TCP |
| Data Format | JSON, XML | XML | Any |
| Style | Resource-based | Operation-based | Function-based |
| Complexity | Simple | Heavy | Simple |
| Flexibility | High | Low | Moderate |
✅ Rationale: REST is preferred for modern web and microservices due to simplicity, scalability, and compatibility with HTTP.
IV. RESTful API Design Best Practices
(Validated from Microsoft, IBM, and GeeksforGeeks)
1. Resource Naming Conventions
- Use nouns, not verbs. ❌
/getUser→ ✅/users - Use plural forms for collections.
/users,/orders/123 - Maintain hierarchical structure for relations.
/users/123/orders/5
2. HTTP Methods (CRUD Mapping)
| HTTP Method | Operation | Example Endpoint | Description |
|---|---|---|---|
| GET | Retrieve | /users | Fetch resource(s) |
| POST | Create | /users | Create new resource |
| PUT | Update/Replace | /users/123 | Replace existing resource |
| PATCH | Partial Update | /users/123 | Modify specific fields |
| DELETE | Remove | /users/123 | Delete resource |
3. Status Codes & Responses
| Code | Meaning | Example Usage |
|---|---|---|
| 200 OK | Successful request | GET success |
| 201 Created | Resource created | POST success |
| 204 No Content | No response body | DELETE success |
| 400 Bad Request | Invalid input | Missing fields |
| 401 Unauthorized | Authentication required | No/invalid token |
| 404 Not Found | Resource missing | /users/999 |
| 500 Internal Server Error | Server issue | Database crash |
4. Versioning
- Use explicit versioning to manage backward compatibility. ✅
/api/v1/users🧱 Rationale: Avoids breaking older clients when API evolves.
5. Pagination, Filtering, and Sorting
Prevent data overload using parameters:
1
GET /users?page=2&limit=10&sort=name&filter=active
page,limit: paginationsort: sortingfilter: conditional queries
6. Authentication & Authorization
- Use stateless tokens (JWT) or OAuth2.
Example header:
1
Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9
7. Error Handling
Return structured error objects:
1 2 3 4
{ "error": "InvalidRequest", "message": "Email field is required" }
Always include meaningful status codes.
8. Documentation & Discoverability
- Use OpenAPI/Swagger for API documentation.
- Include examples and schemas.
- Provide hypermedia links (HATEOAS) for discoverability.
9. Rate Limiting & Throttling
- Prevent abuse and ensure fair usage.
Common headers:
1 2
X-RateLimit-Limit: 100 X-RateLimit-Remaining: 25- Return
429 Too Many Requestswhen exceeded.
10. Security Best Practices
| Principle | Description |
|---|---|
| Use HTTPS only | Prevent eavesdropping |
| Sanitize inputs | Prevent injection attacks |
| Implement CORS carefully | Restrict allowed origins |
| Validate data types and schemas | Avoid malformed payloads |
| Use API keys / tokens | Enforce controlled access |
V. Example: REST API Workflow
Use Case: User Management
| Operation | HTTP | Endpoint | Request Body | Response |
|---|---|---|---|---|
| Create User | POST | /users | { "name": "Alice" } | 201 Created |
| Get All Users | GET | /users | — | [{"id":1,"name":"Alice"}] |
| Get One User | GET | /users/1 | — | { "id":1,"name":"Alice" } |
| Update User | PUT | /users/1 | { "name":"Alice B" } | 200 OK |
| Delete User | DELETE | /users/1 | — | 204 No Content |
VI. RESTful API Testing & Validation
| Tool | Purpose | Example |
|---|---|---|
| Postman / Insomnia | Manual API testing | Validate responses |
| cURL / HTTPie | Command-line API calls | Quick checks |
| pytest + requests | Automated testing | Regression verification |
| Swagger UI | API exploration | Visual test & docs |
VII. Future Directions & Upgrades
| Area | Trend | Why It Matters |
|---|---|---|
| GraphQL | Client-driven queries | Reduces over-fetching |
| gRPC | Binary transport for microservices | High performance |
| OpenAPI 3.1 | Unified schema definitions | Consistency & tooling |
| Serverless APIs | Auto-scalable REST endpoints | Efficient operations |
✅ Summary: REST API Essentials
| Concept | Key Idea | Example / Rationale |
|---|---|---|
| Resource-based | Everything is a resource | /users/123 |
| Stateless | Each request is independent | Easier scaling |
| Cacheable | Enable performance via caching | Cache-Control |
| Uniform Interface | Consistent and predictable | CRUD methods |
| Layered | Multi-tiered architecture | API Gateway → Backend |
| Secure & Versioned | Maintain stability | /api/v1/ with JWT |
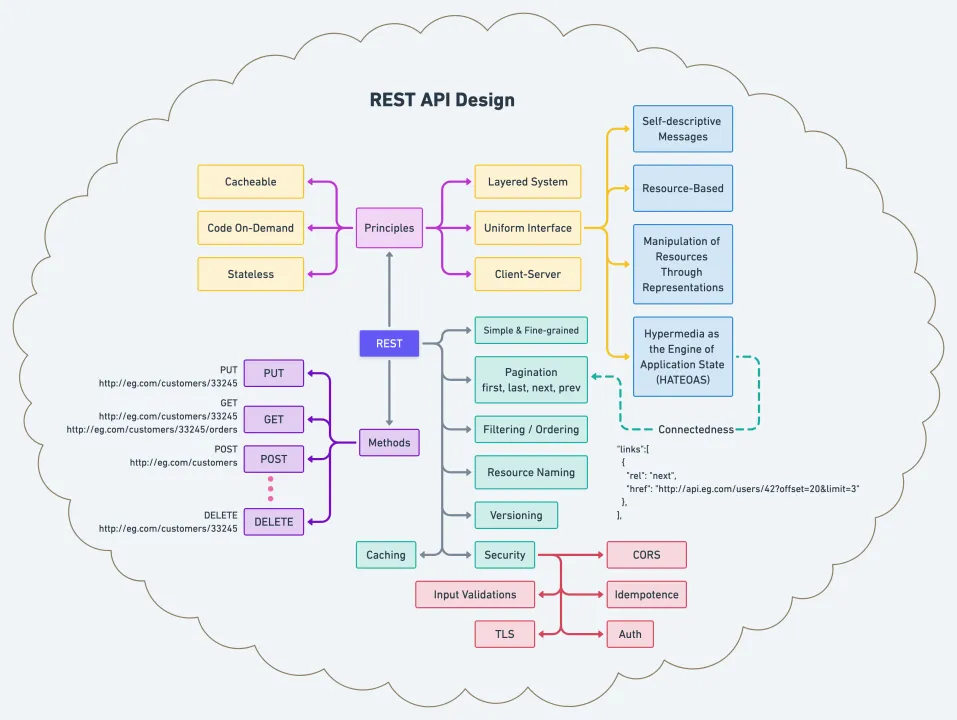 REST API Design Architecture Illustrated
REST API Design Architecture Illustrated
💡 Upgrade Path (Next Steps)
- Practice with FastAPI / Flask REST APIs.
- Add JWT/OAuth2 authentication.
- Generate documentation via Swagger/OpenAPI.
- Use Postman collections for testing workflows.
- Explore GraphQL or gRPC for advanced architectures.
🔗 References
- Wikipedia – REST
- IBM Think: REST APIs
- Microsoft Learn – API Design Best Practices
- GeeksforGeeks – REST API Architectural Constraints
© 2025 — Compiled and validated for clarity, conciseness, and technical correctness.